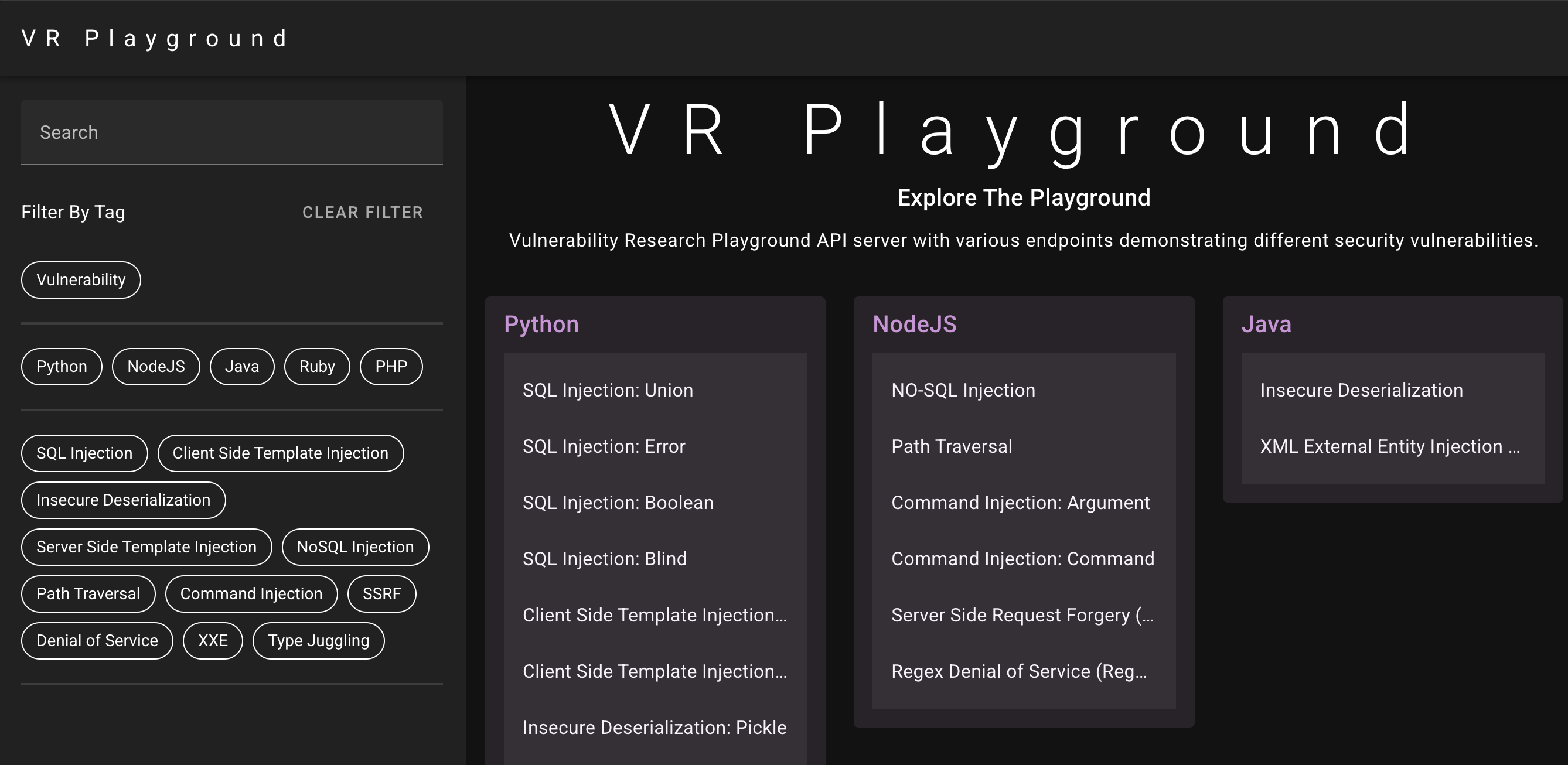
Next-gen, Swagger-driven, polyglot labs for modern AppSec training & research.
Run intentionally vulnerable microservices (Python, Node.js, Java, Ruby, PHP) behind a UI that auto-generates from OpenAPI. Add or modify a lab by editing swagger.yaml—the UI updates itself.
⚠️ Security Warning: This platform contains intentionally vulnerable code. Use only in isolated environments you control. Do not expose publicly.
VRPlayground is a spec-first microservices platform where each service showcases language-specific vulnerability classes side-by-side. Document an endpoint once in OpenAPI, and the frontend renders inputs, examples, and responses automatically—making it simple to:
- Security Researchers: Compare the same vulnerability across different languages and frameworks
- Security Trainers: Create focused, isolated labs for specific attack vectors
- Developers: Learn language-specific security pitfalls in their preferred ecosystem
- Penetration Testers: Practice techniques in realistic, polyglot environments
Document an endpoint once in OpenAPI, and the frontend automatically renders:
- Interactive input forms
- Pre-filled examples
- Response visualization
- Vulnerability explanations
This means zero frontend development when adding new labs—just describe your API and the UI updates itself.
- Polyglot by design: Python, Node.js, Java, Ruby, PHP (easily extensible)
- Spec-driven UI: Auto-generates from
frontend/public/swagger.yaml - Microservices architecture: Isolated, scalable, language-agnostic
- Docker-native: One-command deployment with
docker compose
- Focused labs: Single-purpose endpoints for clear learning objectives
- Language comparison: Same vulnerability, different implementations
- Real-world scenarios: Practical examples beyond basic tutorials
- Extensible platform: Add new languages/services without touching the UI
- Python: SQLi (union/error/boolean/blind), XSS (tag/link/event/code), CSTI (AngularJS/Vue), SSTI (Jinja), Pickle deserialization
- Node.js: NoSQLi (Mongo), Path Traversal, Command Injection, SSRF, Regex DoS
- Java: Insecure Deserialization, XXE
- Ruby: Marshal & YAML deserialization
- PHP: Type Juggling, XXE
See the full spec at /swagger.yaml and all routes under /api.
- Docker & Docker Compose
- Git
# Clone the repository
git clone https://github.com/f5devcentral/VRPlayground
cd VRPlayground
# Start all services
docker compose up -d
# Access the platform
open http://localhost- Main UI: http://localhost/
- API Documentation: http://localhost/swagger.yaml
- API Endpoints: http://localhost/api/
| Service | Port | Purpose |
|---|---|---|
frontend |
80 | Nginx proxy + auto-generated UI |
python-api |
5000 | Python vulnerability labs |
nodejs-api |
3000 | Node.js vulnerability labs |
java-api |
8080 | Java vulnerability labs |
ruby-api |
4567 | Ruby vulnerability labs |
php-api |
80 | PHP vulnerability labs |
mariadb |
3306 | MySQL-compatible database |
mongodb |
27017 | NoSQL database |
VRPlayground's modular design makes it easy to add new vulnerability labs:
mkdir my-language-api
# Add your vulnerable endpoints# Add to frontend/public/swagger.yaml
/my-language/vulnerability-type:
post:
tags: ["My Language", "Vulnerability Type"]
description: "Description of the vulnerability"
requestBody:
content:
application/json:
schema:
type: object
properties:
input:
type: string
example: "malicious_input"Groups can be added by using the 'summary' field for comparison.
# Add the 'summary' field to group endpoints to compare vulnerabilities
/my-language/vulnerability-type:
post:
tags: ["My Language", "Vulnerability Type"]
description: "Description of the vulnerability"
summary: "tag1"# Add to compose.yml
my-language-api:
build: my-language-api
expose:
- "9000"# Add to frontend/conf.d/default.conf
location /api/my-language/ {
proxy_pass http://my-language-api:9000/;
}The UI will automatically pick up your new endpoints from the OpenAPI spec!
- Workshops: Focused, isolated labs for specific attack vectors
- Conferences: Live demonstrations with real-time code changes
- Corporate Training: Language-specific security education
- Vulnerability Research: Compare implementations across languages
- Tool Development: Test security tools against multiple platforms
- Framework Analysis: Understand language-specific security quirks
- Skill Development: Practice techniques in realistic environments
- Tool Validation: Test tools against various technology stacks
- Methodology Refinement: Develop and test attack methodologies
The Project Leaders are:
- Tomer Zait aka realgam3
- Dimitri Belski
We welcome contributions! VRPlayground is designed to be community-driven:
- Add new languages: Create services in your preferred language
- Enhance existing labs: Improve vulnerability implementations
- Documentation: Help improve guides and examples
- UI improvements: Enhance the auto-generated interface
- Keep labs intentionally vulnerable but well-documented
- Follow the existing OpenAPI specification format
- Ensure Docker compatibility
- Add comprehensive examples and explanations
Apache 2.0 - See LICENSE file for details.