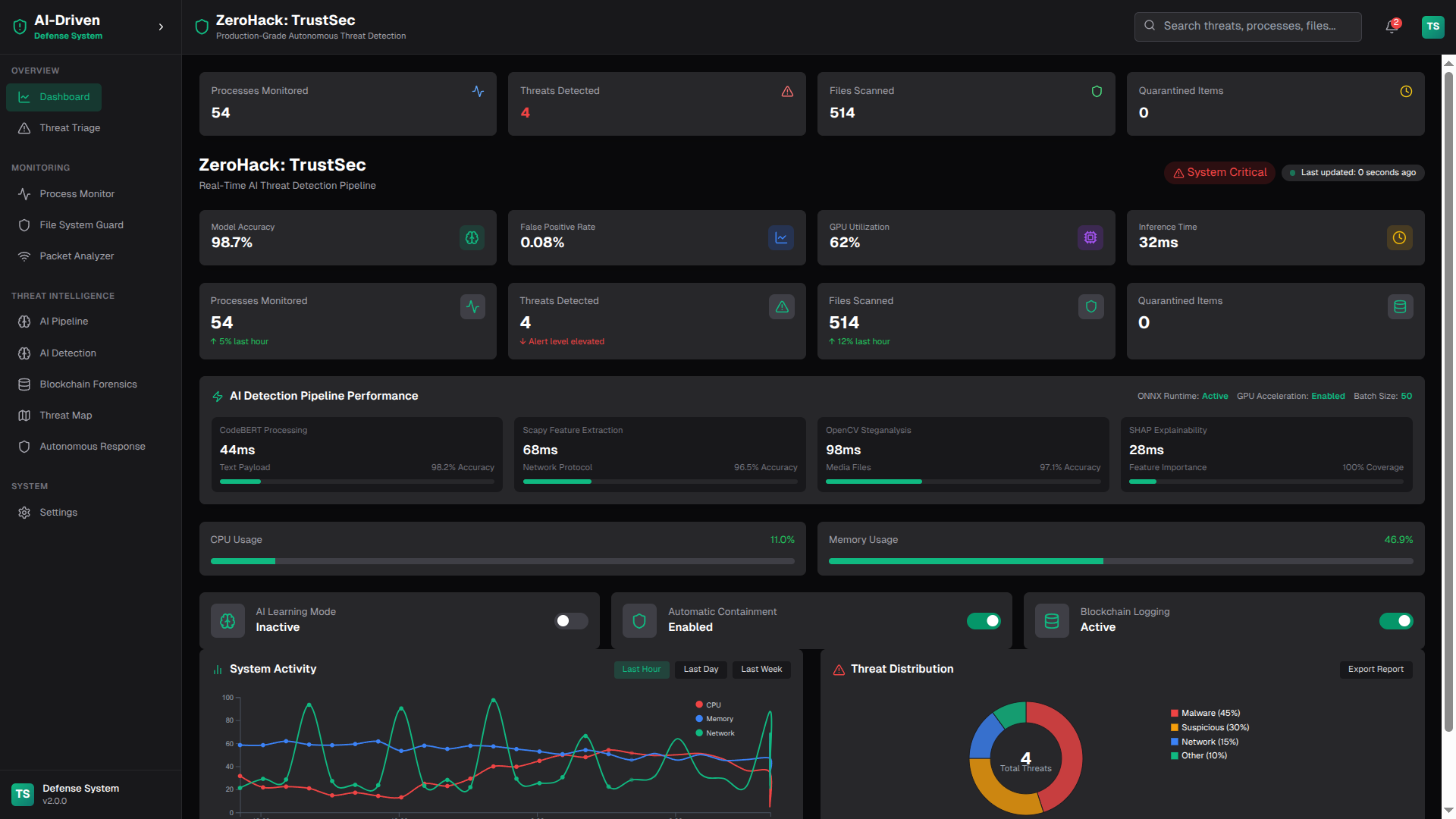
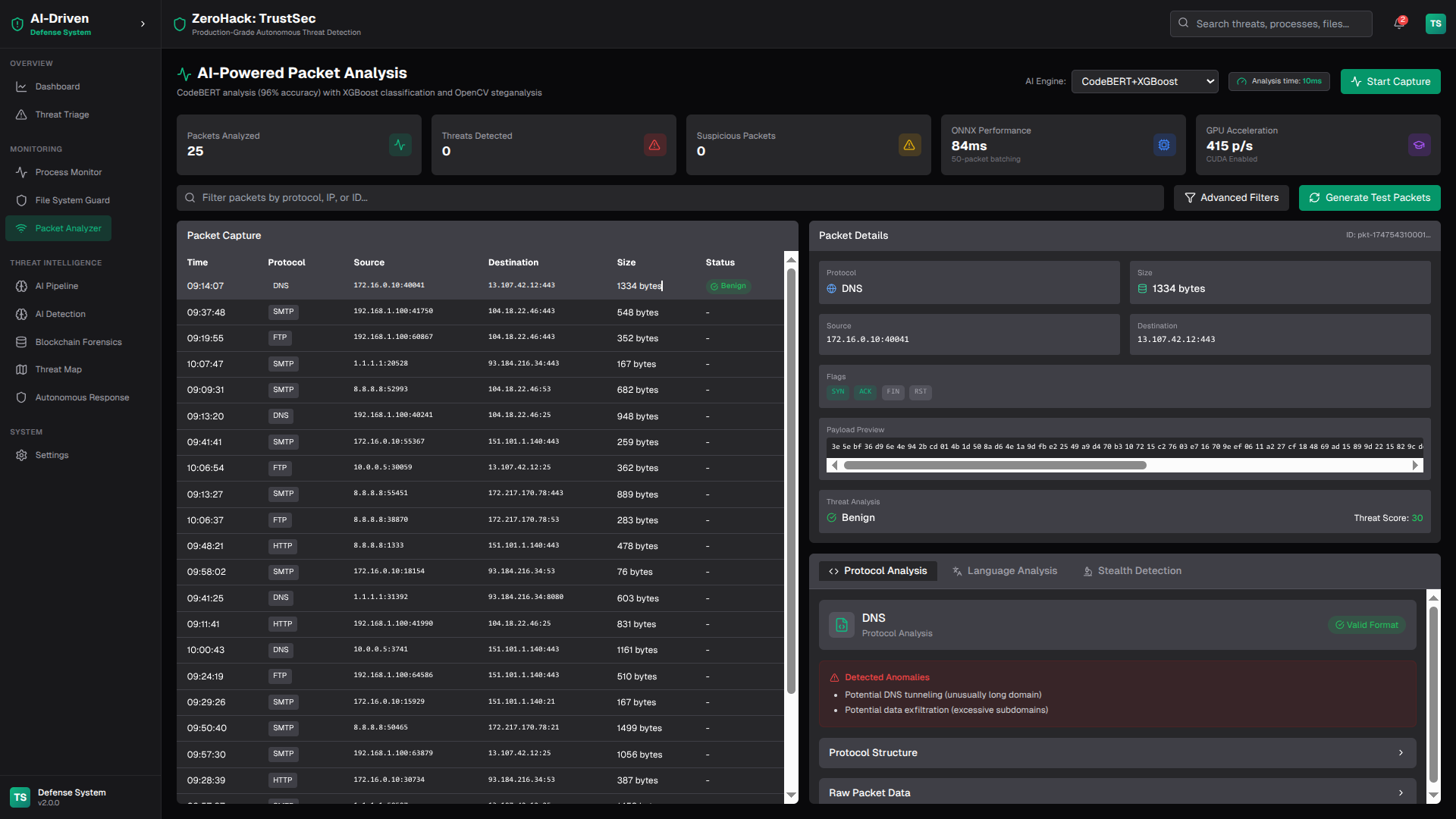
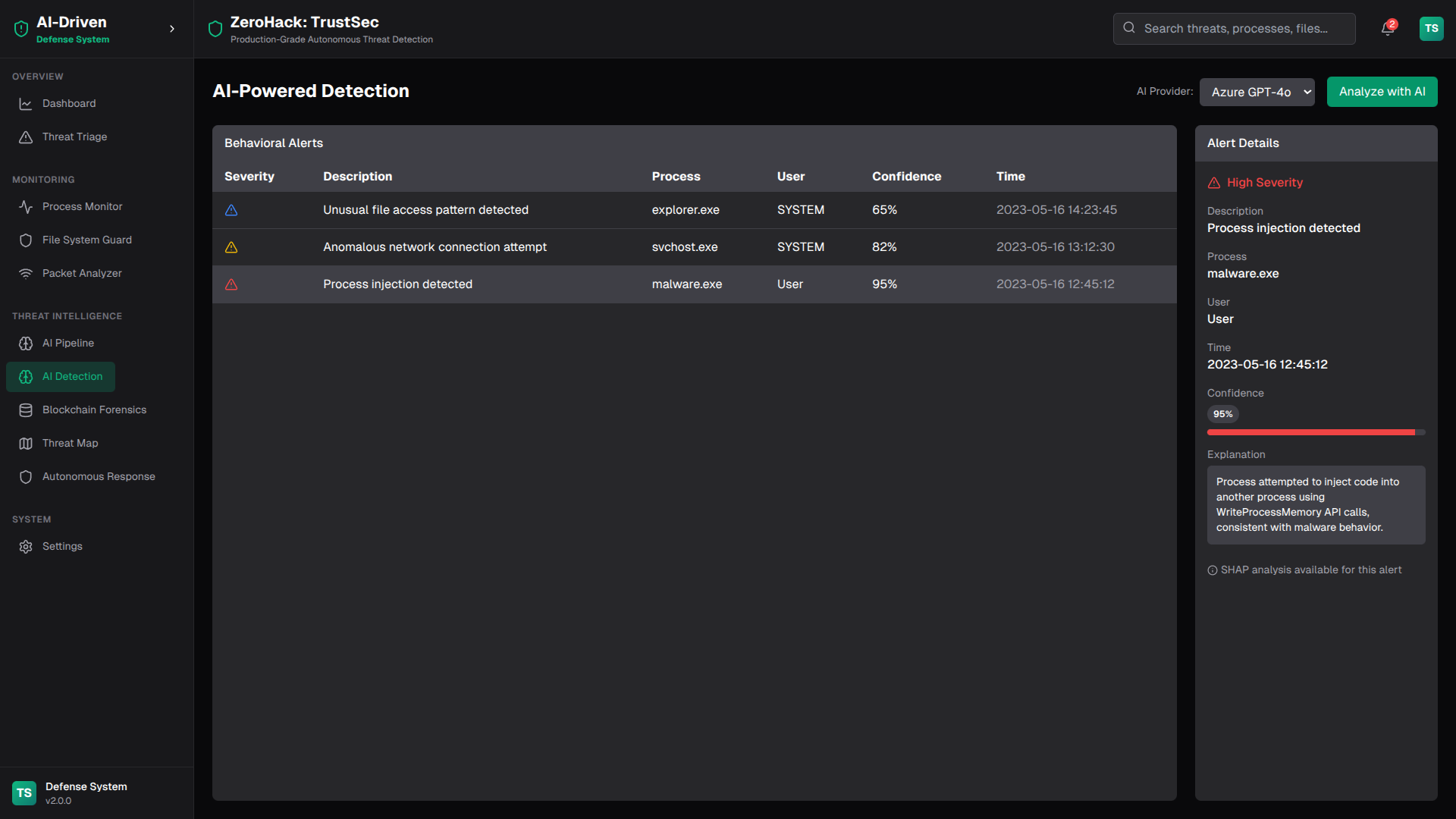
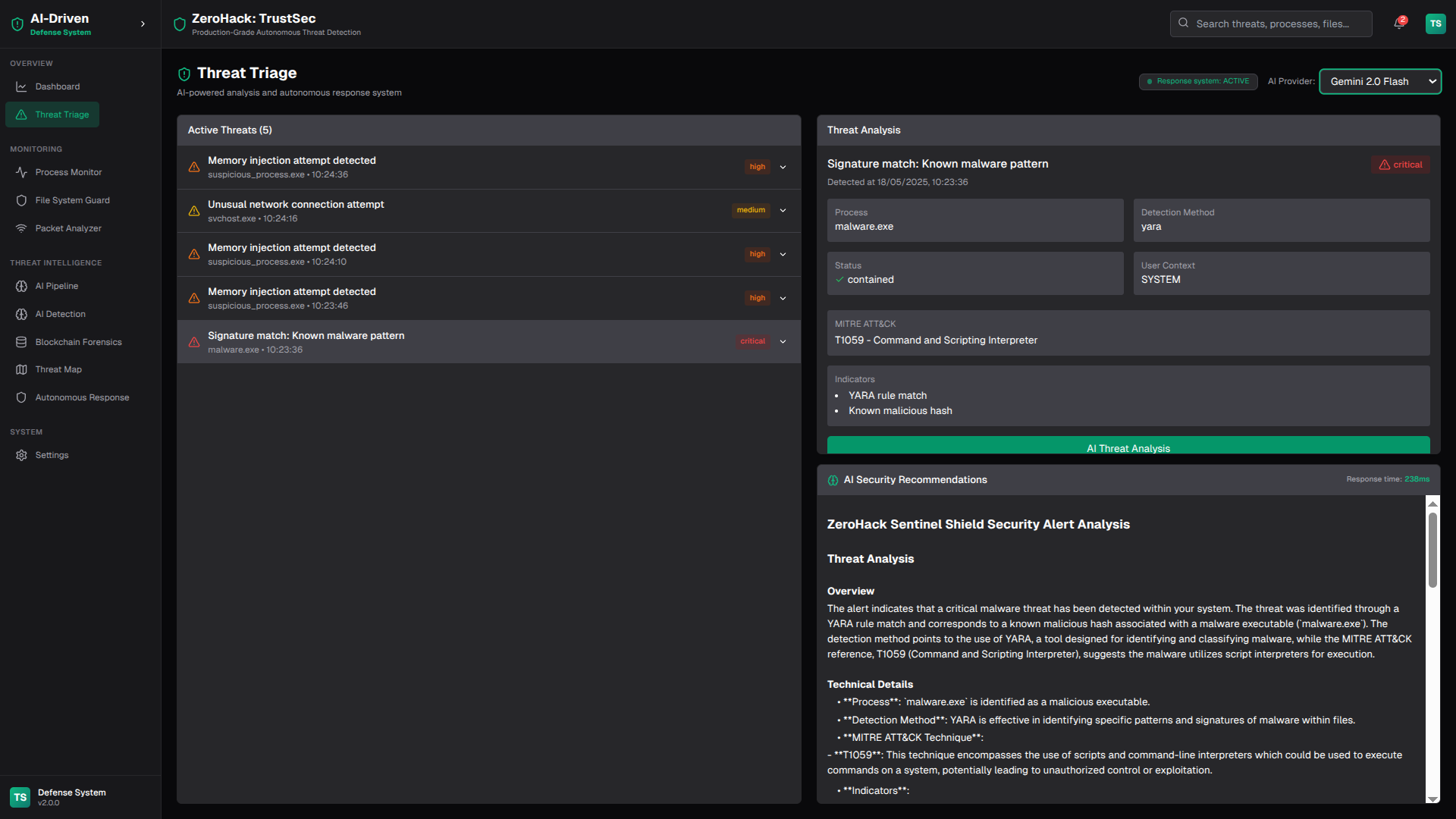
ZeroHack is a full-stack, next-generation cybersecurity platform that leverages multi-layered AI and blockchain-based forensics to detect, analyze, and autonomously respond to modern cyber threats in real time.
Traditional security systems often:
- Fail to detect advanced persistent threats (APTs) such as stealthy or fileless malware.
- Rely on static rules that attackers can easily bypass.
- Store logs in modifiable formats, compromising forensic reliability.
- Respond slowly due to lack of automation.
ZeroHack addresses today’s cyberattack landscape through:
- AI-Driven Detection: Uses natural language processing (NLP), deep learning (CNN/RNN, LSTM, Autoencoders), and transformer models to detect malicious content in traffic, payloads, steganography, and unknown protocols.
- Advanced Packet Analyzer: Analyzes payloads, image-based threats, and novel data patterns using deep learning and entropy analysis.
- Immutable Logging: Stores verified threat incidents on blockchain (Ethereum/Hyperledger) for tamper-proof audit trails.
- Smart Contracts: Automate response actions such as IP quarantine and incident logging.
- Capture Payload or Log File: Via user upload or live network feed.
- Preprocess Input: Feature extraction, header/payload parsing.
- AI-Based Threat Detection:
- NLP/CodeBERT: Detects obfuscated command injections and text-based threats.
- CNN/RNN: Identifies steganography, covert channels, and image-based threats.
- Autoencoders: Flags unknown protocols or anomalies.
- Threat Scoring & Classification
- Automated Response: Decide (Allow, Monitor, Quarantine) based on threat score.
- Blockchain Logging: Log incidents using smart contracts for forensic immutability.
- Dashboard Visualization: Real-time threat monitoring and threat history.
AI & ML
- PyTorch, TensorFlow, Scikit-learn
- BERT, LSTM, CNN, RNN, CodeBERT (NLP/text/code analysis)
Network & Data
- Scapy, CICFlowMeter (packet analysis)
- Pandas, NumPy
- Datasets: CICIDS2017, NLP Cybersecurity, JPEG StegoChecker
Frontend
- React.js (UI/dashboard)
- Tailwind CSS / Material UI (design)
- Web3.js (blockchain integration)
Backend & Security
- Flask (API server)
- Web3.py (blockchain/contract interaction)
- Solidity Smart Contracts (Ethereum)
- Hyperledger (optional blockchain logging)
Testing & Simulation
- Metasploit, Kali Linux, Slowloris
- Protocol Parsers: Deep protocol inspection for HTTP, DNS, SMTP, FTP, with anomaly detection for attacks like SQL injection, XSS, DNS tunneling, email exfiltration, and FTP abuse.
- AI Pipeline: Multi-stage pipeline with CodeBERT for text/code, CNN for image payloads/steganography, Autoencoders for protocol anomaly detection.
- Blockchain Forensics: Stores PCAPs and incident references on blockchain; dashboard shows chaincode/smart contract status (with IPFS for storage).
- Entropy & Feature Analysis: Shannon entropy and feature extraction for detecting obfuscation and unknowns.
- User Dashboard: Real-time protocol analysis, anomaly reporting, and raw packet visibility.
- Self-Healing Infrastructure: Auto-recovery and isolation during incidents.
- Real-Time Threat Intelligence Feeds: Integration with global sources.
- Federated Learning: Distributed training without sharing raw data.
- Browser Extension: Endpoint threat detection for browsers.
ZeroHack is a decentralized, AI-powered security platform that adapts and defends in real time—offering intelligent, autonomous, and tamper-proof cyber protection.