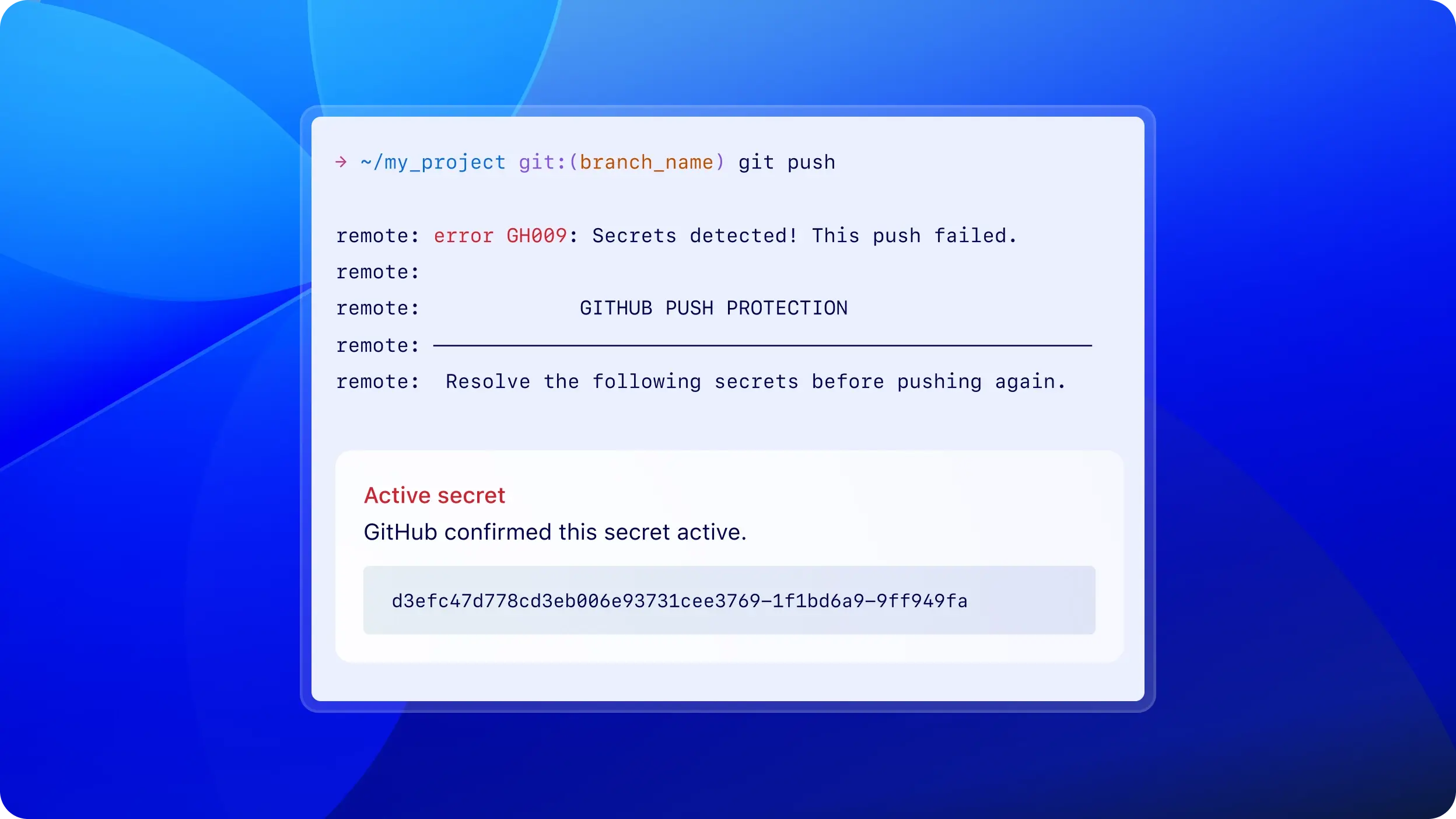
Push protection automatically blocks secrets before they reach your repository, keeping code clean without disrupting workflows.

Keep your secrets secret
GitHub Secret Protection continuously monitors your GitHub perimeter, helping prevent exposures, protect credentials, and ship securely.
4.4M Secrets prevented from leaking on GitHub in 2024
150+ Industry partners, working together to mitigate risk for the developer community
39M Secret leaks detected with Secret Protection in 2024
Prevent accidental secret exposure
across your repositories
Block leaks before they happen
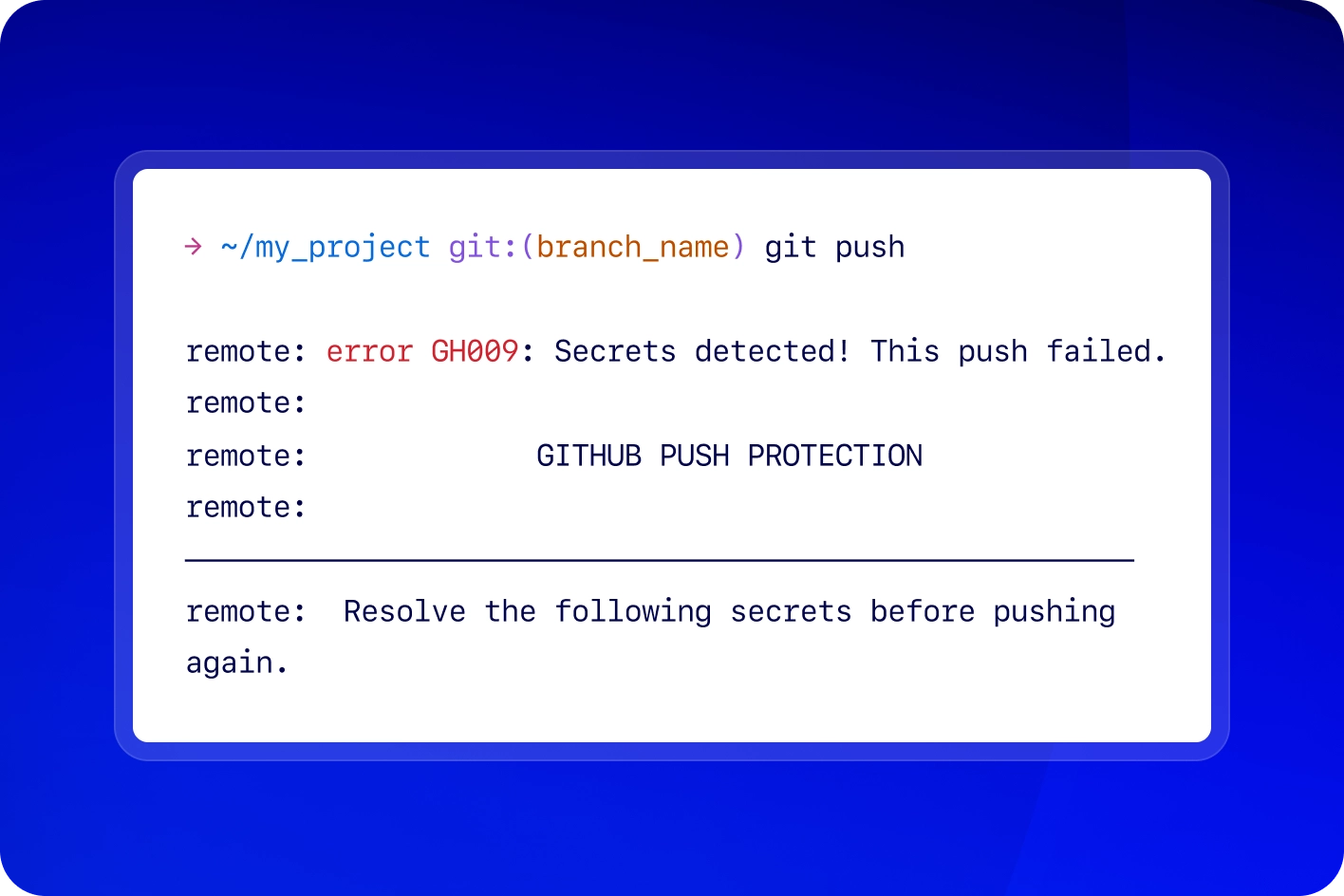
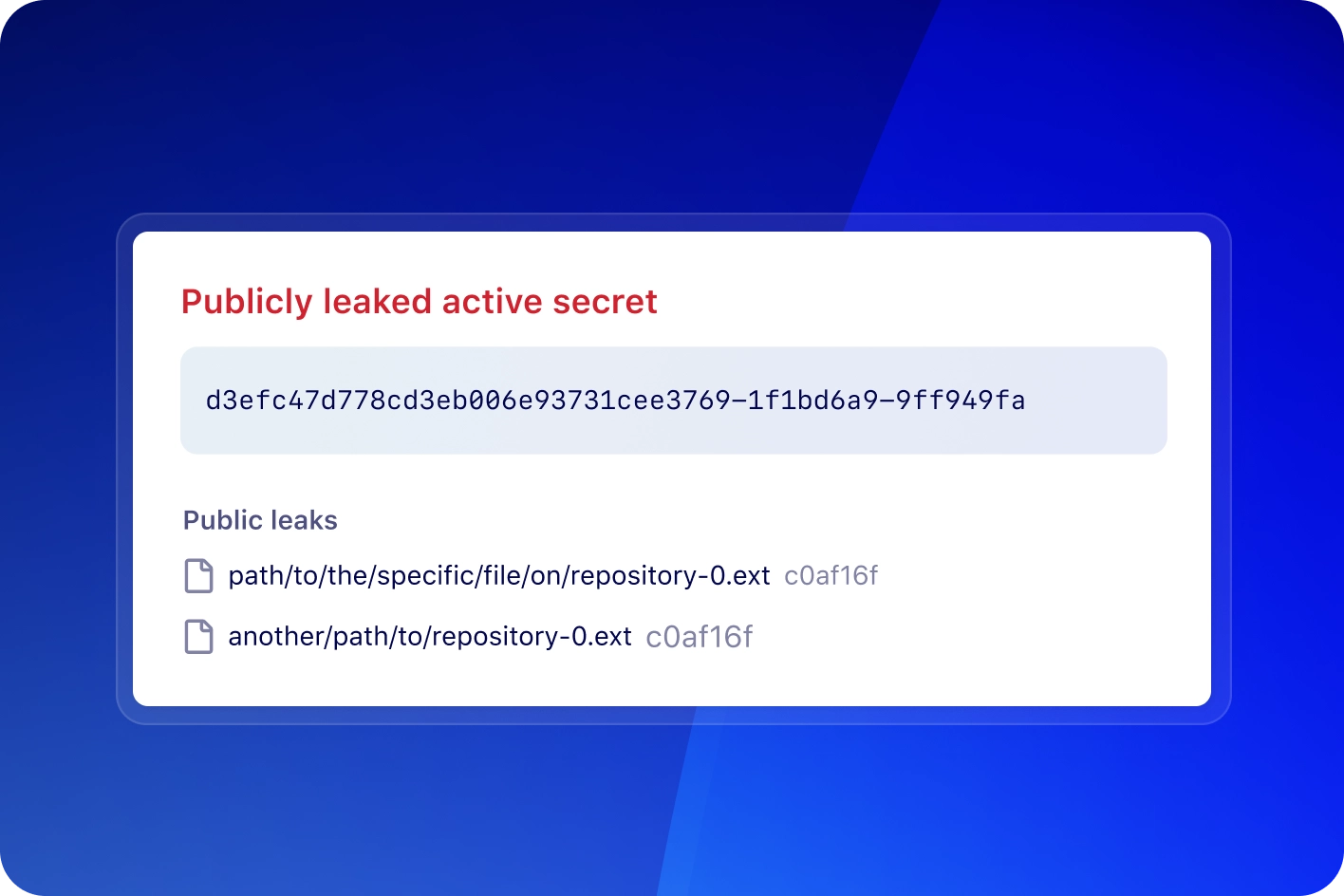
Find the threats that others miss
Detect secrets in issues, discussions, and more with secret scanning. Metadata like validity checks and public leaks help prioritize active threats.
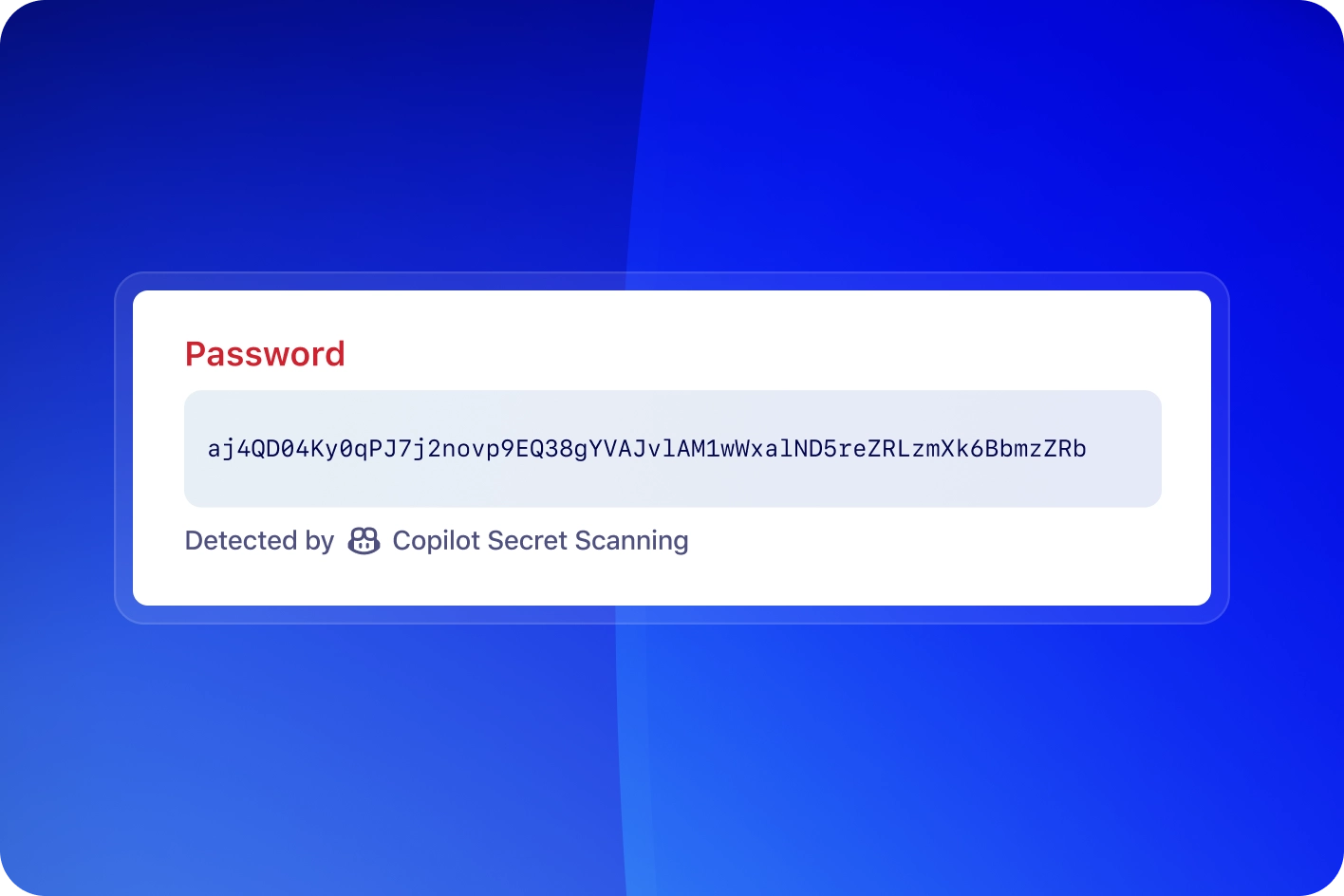
Give Copilot the heavy lifting
GitHub Copilot finds elusive secrets like passwords without the false positives. It detects secrets that traditional secret detectors can't catch, providing an additional layer of security.
Standardize enforcement, simplify compliance
Manage policies like delegated bypass for push protection, alert dismissal restrictions, and built-in enablement configurations, simplifying security enforcement at scale.
Powered by a global security partnership
GitHub partners with 150+ providers to mitigate risks and ensure the highest level of detection accuracy.
Learn about the secret scanning partner program
Safer code for everyone
Whether you're securing an open source project or strengthening your enterprise codebase, Secret Protection helps you keep secrets out of your code.
Resources to get started
FAQs
What is GitHub Secret Protection?
GitHub Secret Protection detects and prevents secret leaks continuously in real-time, proactively blocking sensitive credentials from being pushed to a repository with push protection. With a remarkably low false positive rate and approximately 150 service provider integrations, it enables rapid credential revocation and rotation, enhancing developer productivity.
What is the secret risk assessment?
The secret risk assessment provides a free, comprehensive overview of an organization’s secret leak footprint across its GitHub repositories. By analyzing repositories for exposed secrets, it helps admins and developers understand their exposure to potential security risks and offers actionable insights for remediation.
What is push protection?
Push protection is designed to prevent sensitive information, such as secrets or tokens, from being pushed to your repository in the first place. It proactively scans your code for secrets during the push process and blocks the push if any are detected.
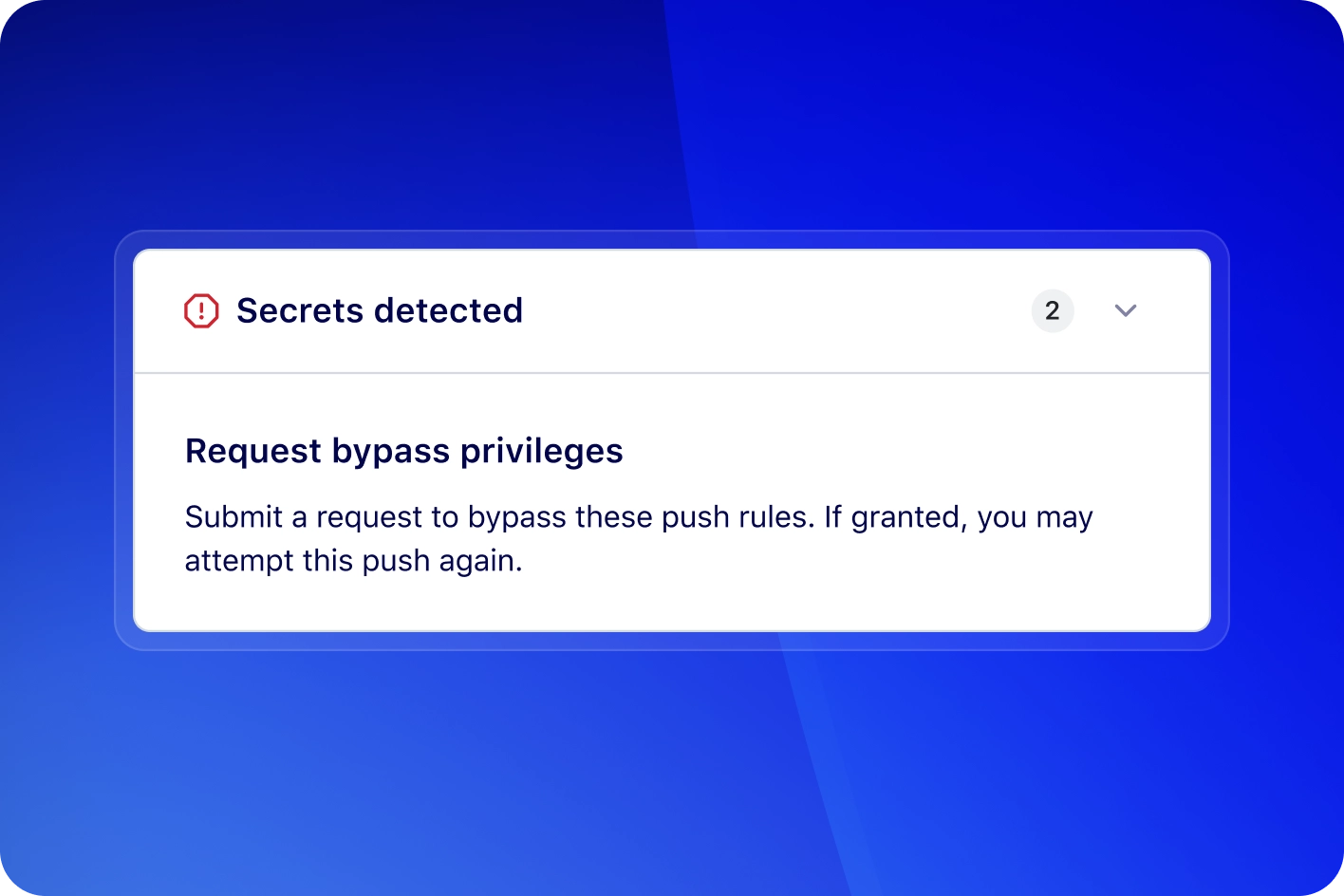
What is delegated bypass for push protection?
Delegated bypass introduces an approval process for developers to bypass push protection. Anyone opting to bypass a push protection block will need to submit a request to a designated group of reviewers, ensuring any risky secrets are not accidentally leaked.
What are secret scanning validity checks?
Validity checks help you determine whether detected secrets are still active, enabling developers and security teams to prioritize their response effectively. When a secret is flagged, the system verifies its validity to confirm whether the secret is active or inactive.
What is the secret scanning partnership program?
The secret scanning partnership program allows service providers to secure their token formats by enabling GitHub to scan public repositories and npm packages for exposed secrets. When a secret is found in a public repo, GitHub sends an alert directly to the service provider, who can then validate and take appropriate action.